A recent data breach exposed sensitive information including social security numbers of billions of people worldwide, potentially leading to a significant increase in identity theft and cybercrime. Here’s what you need to know and what to do about it.
The USDoD hacking group has breached National Public Data (NPD), a data broker that offers personal information for background checks. This is no ordinary data breach.
More than 2.7 billion records were stolen, containing an unprecedented amount of information.
The breach compromised 2.7 billion records, including:
- Names
- Addresses
- Dates of birth
- Social security numbers
- Phone numbers
Teresa Murray, director of Consumer Watchdog at PIRG, said this breach is more concerning than previous incidents because of the size and sensitivity of the data.
“If this is in fact the whole dossier about all of us, it is certainly much more worrying [than prior breaches],Murray explained to the Los Angeles Times“And if people in the past haven't taken precautions, which they should have, then this should be a warning to them.”
Despite the severity of the breach, National Public Data has not yet sent formal notices to affected individuals. The company has claimed to have cleaned up its entire database of personal information and has chosen to remove non-public personal information.
However, it is unclear whether this measure is sufficient to limit the risks posed by the infringement.
Risks and implications
The leaked information is a goldmine for cybercriminals, who provide almost all the data they need to commit identity fraud. With social security numbers, dates of birth and addresses, criminals can create fraudulent accounts, apply for loans and manipulate existing accounts.
Although email addresses and photos of driver's licenses were not found in the breach, the missing data can be supplemented with information from previous breaches.
The consequences of such a breach can be catastrophic. Identity theft can result in significant financial loss, damage to credit scores, and a lengthy recovery process for victims.
Furthermore, the ease with which this data can be weaponized underscores the urgent need for stronger security measures.
For example, a specific threat related to exposed data is the risk of a SIM swap attack. In a SIM swap attack, cybercriminals use stolen personal information to convince your mobile provider to port your phone number to a new SIM card.
Once they have your number, they can intercept SMS-based two-factor authentication codes and gain access to your accounts. Given the detailed personal information leaked in this breach, the likelihood of such attacks increases significantly.
Urgent steps to protect yourself
To protect yourself from SIM swap attacks, set up a PIN or passcode with your mobile provider and be alert for unusual activity, such as sudden loss of coverage.
Next, placing a credit freeze with the three major credit bureaus in the U.S. prevents criminals from opening new accounts in your name. It’s free and restricts access to your credit report.
It’s also crucial to monitor your accounts. Identity theft protection services can monitor your accounts and scan the dark web for compromised personal information. While these services often cost money, companies that suffer data breaches sometimes offer them for free to affected customers.
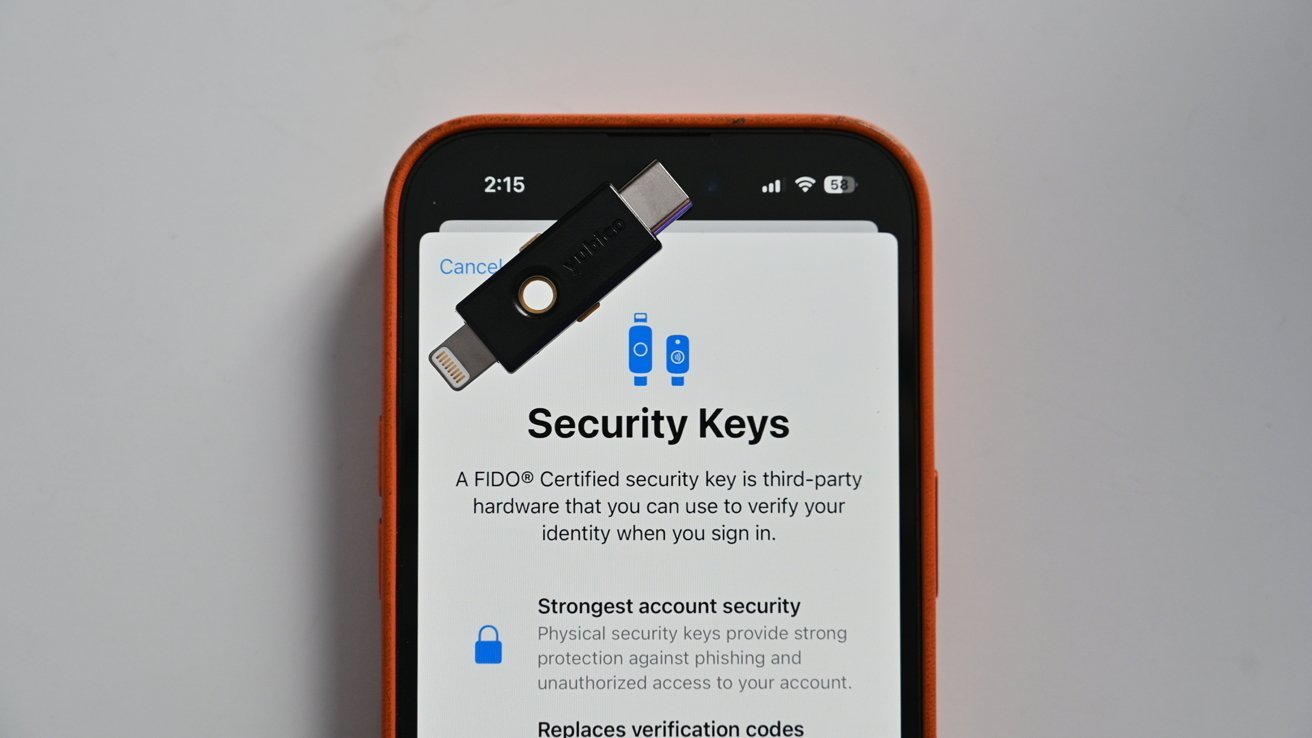
Strengthen your passwords with unique, strong passwords. Consider using a password manager. Enable two-factor authentication (2FA) using codes from an authenticator app or a hardware security keyWith such a code, it is virtually impossible for attackers to hack your iCloud account, even if they have your password and a fake SIM card.
A security key is a physical device that you insert into your computer or connect to your smartphone. Unlike codes sent via text message or apps, security keys are immune to phishing attacks because they only work with registered websites.
What makes security keys particularly effective is their immunity to phishing attacks. Traditional two-factor authentication methods, such as SMS codes, can be intercepted by attackers masquerading as legitimate services, such as in a SIM swap attack.
Security keys are different, however. They are tied to the specific websites you register them on, meaning they won’t work on fraudulent sites that try to imitate legitimate ones.
Even if a hacker manages to steal your password, they cannot access your account without the physical key.
By taking measures such as freezing credit, strong passwords, two-factor authentication, and using security keys, you can significantly reduce your risk of becoming a victim.
Stay vigilant, keep your security practices up to date, and remember that in the digital world, your best defense is to always be one step ahead of potential attackers. By taking these precautions today, you can save yourself from potential headaches and financial losses in the future.